The open-source user interface Wireshark (formerly Ethereal) is a network protocol analysis program.
The program tracks all network traffic on an interface, analyzes it, breaks it down into coherent pieces, and displays it “live”.
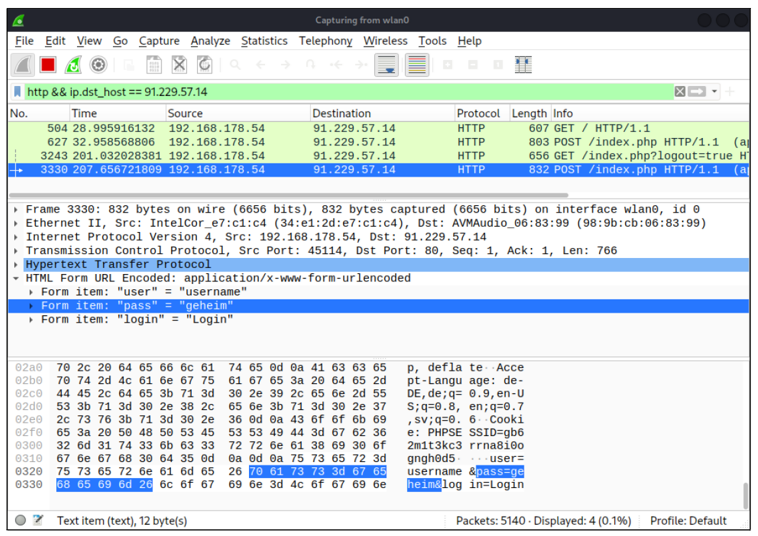
Because direct observation is mostly impossible with the large amounts of data that are generated, the program offers on the one hand the possibility to filter the data flow very specifically by certain packets (e.g., by all HTTP requests or by IP addresses). On the other hand, you can save the data for later analysis.
By its very nature, there are many possible applications for Wireshark: Developers use it to explore how network protocols work and search for bugs in their own programs.
Network administrators can use the program to search for suspicious data packets that indicate malware on a computer or a backdoor in a program.
For attackers, Wireshark is a goldmine, especially if they manage to run the program on a gateway for the target’s internet access. One conceivable approach is for the attacker to offer a free WLAN hotspot and hope that the target will use it. Conveniently, Wireshark can also be installed on the Raspberry Pi, which is well suited for such applications.
Wireshark reaches its limits when the network traffic is encrypted. This is the case, for example, in HTTPS, SSH, or VPN connections. Wireshark can of course display such packets including all metadata, but due to the encryption the content of such packets is not readable in plain text.
Installation
In Kali Linux, Wireshark is already installed by default. For most other Linux distributions, Wireshark is available as a package that can be installed using apt or dnf, depending on the distribution. Downloads for Windows and macOS can be found at https://www.wireshark.org/download.html.
When installing on Linux, depending on the distribution, a prompt appears (see the figure below) asking whether the program is only used by root (this used to be the normal case) or whether it may also be run by ordinary users if they are members of the wireshark group. The second variant has the advantage that less code needs to be executed with root privileges. You should therefore choose Yes. If necessary, you can repeat this configuration in Kali Linux, Debian, and Ubuntu with dpkg-reconfigure wireshark-common.
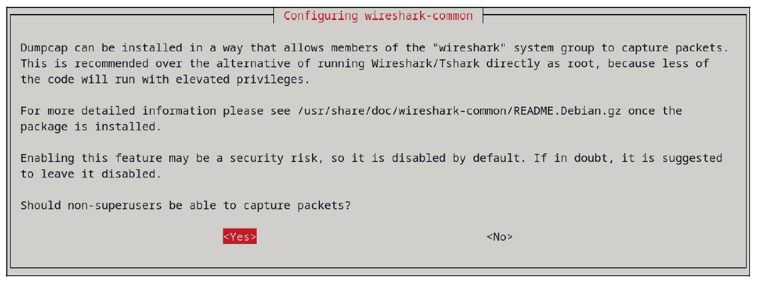
As an administrator, you must then add the relevant users to the wireshark group. If you run Kali Linux on the Raspberry Pi, add the default user kali to this group; otherwise, add the user you set up during the Kali installation:
sudo usermod -a -G wireshark kali
This user must then log out and log in again and can then use Wireshark directly. More details about this mode can be found in /usr/share/doc/wireshark/README.Debian and at https://wiki.wireshark.org/CaptureSetup/CapturePrivileges.
Basic Functions
When you start the program, double-click the network interface you want to monitor. Thereafter, a rapidly growing list of packages appears at the top of the Wireshark window. Select one of the packets and the second area of the window will show metadata about the network packet (frame size, packet and protocol type, sender and receiver address, etc.); the third area shows the actual data in hexadecimal format as well as text.
The flood of data is initially overwhelming. Now it’s a matter of using display filters to select exactly the data you actually want to see. To do this, you must specify the search expression in the line below the button bar. If the search expression is syntactically correct, the input line is highlighted in green, otherwise in red. The filter expression is formulated similar to an if condition in a programming language.
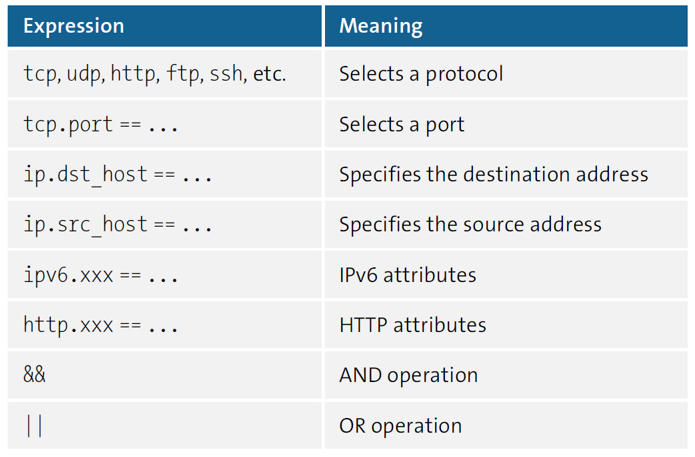
For example, the following expression means that Wireshark should only display packets that match the HTTP protocol and where the source or destination address is a specific IP address:
http && (ip.dst_host == 1.2.3.4 || ip.src_host == 1.2.3.4)
Wireshark provides an almost endless number of possibilities to formulate conditions for any kind of IP packets, protocols and states. For input, you can open the Display Filter Expression dialog via the Analyze menu.
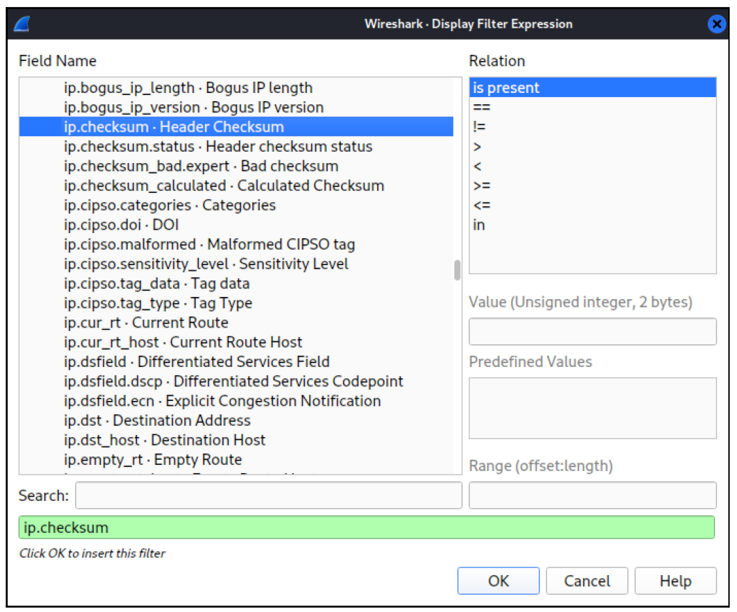
Another input facilitator is integrated directly into the Wireshark user interface: if you right-click an IP address, protocol name, or other piece of information in the interface, you can use the context menu to expand the filter accordingly.
Color Games
Wireshark sets the lines of the package overview in different colors by default. If the colors are too confusing for you, you can easily deactivate the color display via the Colorize Packages button and activate it again just as quickly.
You can see which color applies to which type of package via View > Coloring Rules. In this dialog, you can also change the rules, add your own rules, and save or load the rule set.
Current versions of Kali Linux use dark mode, which means that all elements of graphical interfaces are displayed in dark colors. This is not only in line with the zeitgeist, but also with all hacker prejudices. Wireshark takes over this setting.
If you want to run Wireshark in light mode, as shown in the screenshots in this book, it isn’t sufficient to switch Kali Linux to light mode via Settings > Appearance Style. This is because unlike many other programs, Wireshark uses the Qt library. The color palette of the Qt programs must be set separately in the qt5ct program. Then it works.
Working Techniques
Huge amounts of data accumulate on a busy network node in a short period of time. Wireshark records the data like a recorder and keeps it in the memory. Of course, this is based on the assumption that enough RAM is available. In real life, it’s expedient to end the recording as quickly as possible via the red Stop button. Afterward, the recording can be analyzed.
Via File > Save, you can save a completed recording for later analysis. You should use Wireshark’s own format in *.pcapng files and also select the Compress with gzip option. Later you can load the file again via File > Open—for example, on another, more powerful computer—if you want. Wireshark can also analyze files recorded with other programs, such as tcpdump or Sniffer.
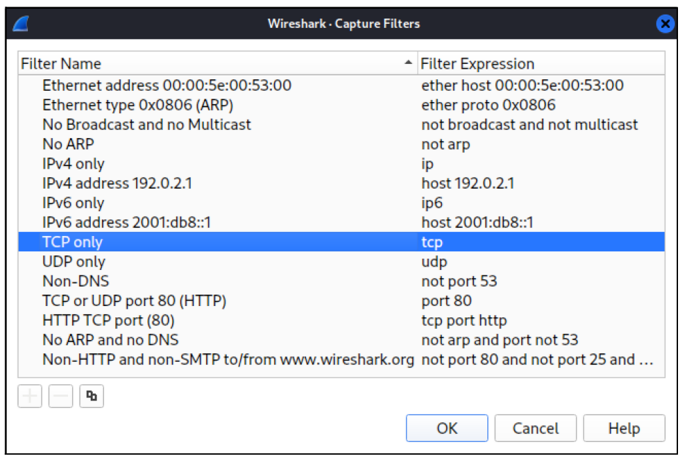
To reduce the amount of data from the start, Wireshark allows you to filter a recording. To do this, select a filter under Capture > Capture Filter (see figure below). This significantly reduces the amount of data Wireshark has to memorize, but unlike the display filter explained previously, this decision is final: what isn’t recorded can’t be inserted later if it turns out that further packets would be required for analysis after all.
Wireshark offers far more analysis functions than this section implies. If you want to learn more about the program, you should study the comprehensive online documentation at https://www.wireshark.org/docs.
In addition, there are a lot of Wireshark videos available on YouTube, and there are also several excellent books to choose from.
Alternatives
Wireshark is the best known program within its category, but there are of course plenty of alternatives. Free of charge, but only executable in the Microsoft universe, is Microsoft Network Monitor. The program is still popular today, although development ended in 2010 with version 3.4. It’s still available to download at http://s-prs.co/v569620.
In the meantime, as the successor to the Network Monitor, Microsoft has developed the *Microsoft Message Analyzer*. It could group packages/fragments that belong together better. However, this tool has also been discontinued and is no longer available for download.
The Windows program Fiddler (https://www.telerik.com/fiddler) is specially optimized for HTTP and HTTPS traffic, and it’s also free. (There have been beta versions for Linux and macOS for years. Whether these will ever become stable program versions is not foreseeable.) Fiddler acts as a proxy server and can also manipulate analyzed programs— for example, to perform man-in-the-middle attacks.
For friends of the command line, there are of course also various tools that perform at least partial tasks of Wireshark:
- The tcpdump and ngrep commands filter the TCP, UDP, or ICMP packets flowing through a network interface and record the desired packets in a file. You can analyze them later with another tool, such as Wireshark.
- ettercap, despite a much simpler interface, can be used like Wireshark to filter out interesting information (passwords and the like) from network traffic. However, the real specialty of the program is the execution of man-in-the-middle attacks.
Editor’s note: This post has been adapted from a section of the book Hacking and Security: The Comprehensive Guide to Penetration Testing and Cybersecurity by Michael Kofler, Klaus Gebeshuber, Peter Kloep, Frank Neugebauer, André Zingsheim, Thomas Hackner, Markus Widl, Roland Aigner, Stefan Kania, Tobias Scheible, and Matthias Wübbeling.




Comments